
Establishing a Robust Security Baseline: A Practical Guide
A security baseline serves as the foundational framework for robust cybersecurity, providing a standardized configuration for systems and applications...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

A security baseline serves as the foundational framework for robust cybersecurity, providing a standardized configuration for systems and applications...
This comprehensive guide provides a strategic roadmap for optimizing cloud software licensing costs, covering various licensing models and offering pr...
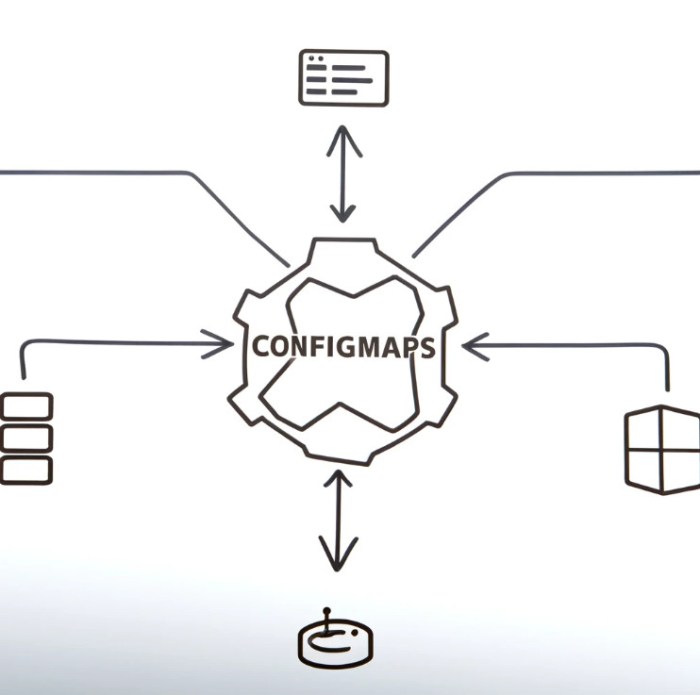
This guide explores the critical role of ConfigMaps in managing application configurations within a Kubernetes environment. By leveraging ConfigMaps,...
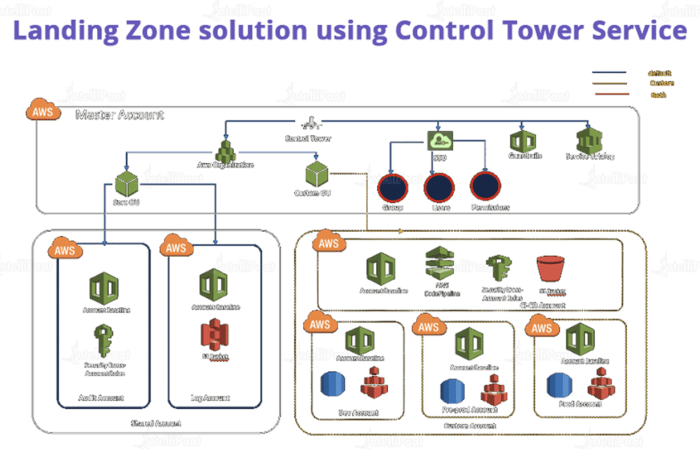
Establishing a secure and compliant landing zone is critical for a strong cloud foundation. This guide outlines a structured approach to designing a r...

Navigating the complexities of cloud security requires a robust understanding of forensic principles. This comprehensive guide explores the unique cha...

Infrastructure as Code (IaC) is transforming modern IT by allowing infrastructure management through code, revolutionizing how we build, manage, and s...
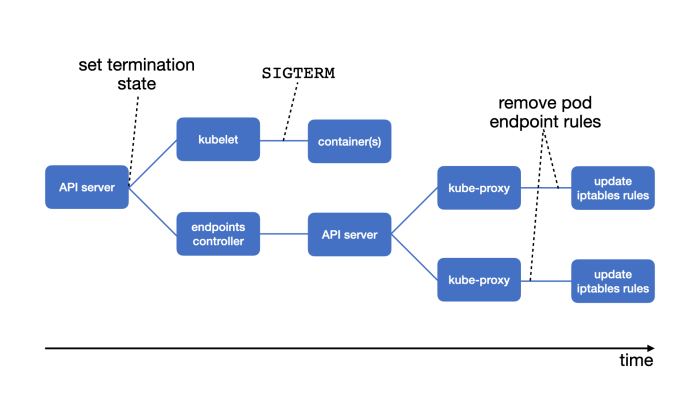
This article provides a comprehensive guide to Kubernetes Network Policies, explaining their fundamental purpose in securing cloud-native environments...
The "Infinite Bandwidth Fallacy" can lead to significant project delays, budget overruns, and system performance issues if left unaddressed. This arti...
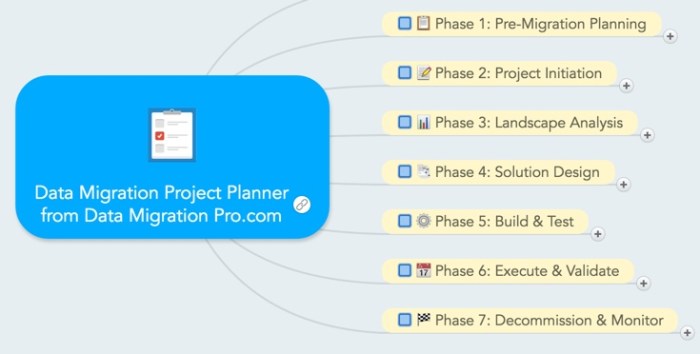
In today's evolving technological environment, successfully aligning migration initiatives with long-term business goals is paramount. This process de...

This comprehensive guide provides a roadmap for organizations seeking to adopt a DevOps culture, covering everything from fundamental principles and r...
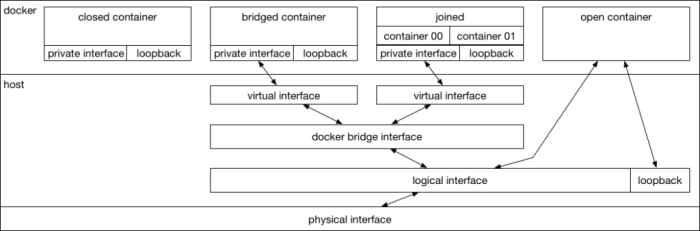
Mastering Docker networking is essential for building robust and scalable containerized applications. This comprehensive guide delves into the core pr...
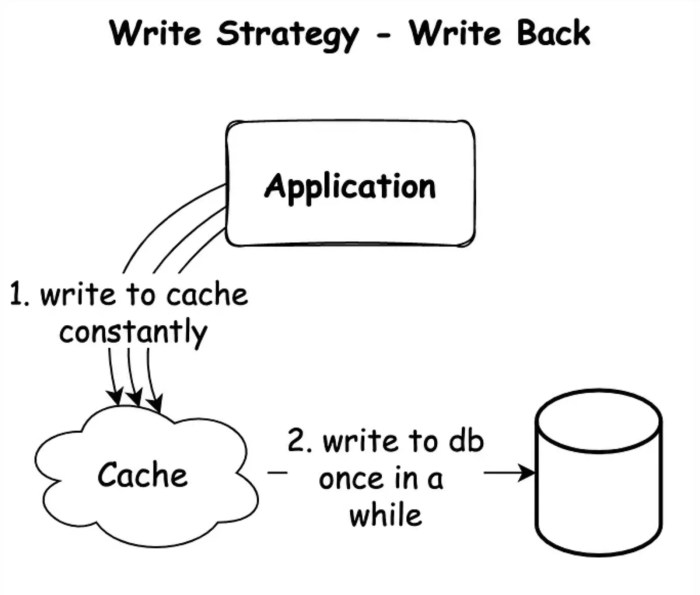
This article delves into the crucial concepts of write-through and write-back caching, two fundamental strategies for optimizing data access and impro...