Conducting Regular Cloud Security Risk Assessments: A Step-by-Step Guide
To proactively secure your cloud environment, regular security risk assessments are essential. This guide outlines the key steps involved in identifyi...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

To proactively secure your cloud environment, regular security risk assessments are essential. This guide outlines the key steps involved in identifyi...
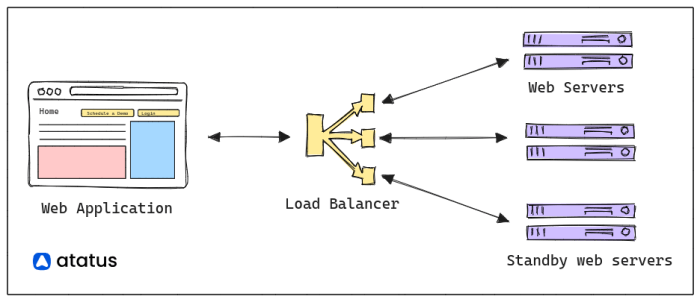
Distributed systems are inherently vulnerable to network unreliability, posing significant challenges to application performance and functionality. Th...
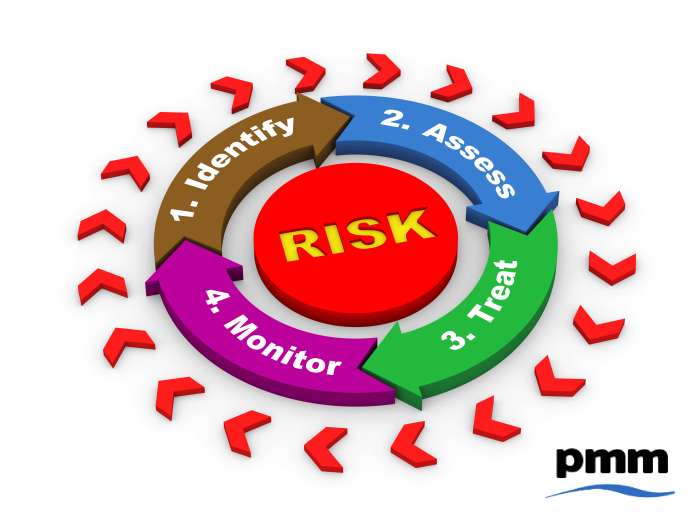
Cloud migration offers substantial benefits, yet it also introduces a complex web of risks that must be proactively addressed. This article delves int...

Cloud computing's diverse providers and billing structures can create a fragmented view of your spending, hindering effective cost management. This ar...
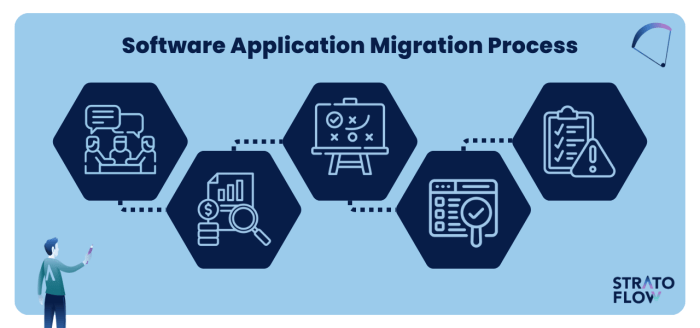
Application migration demands a proactive strategy to maintain application performance. This guide provides a comprehensive framework for pre-migratio...

This article provides a comprehensive overview of strategies to improve deployment frequency, a critical factor in modern software development. It exp...
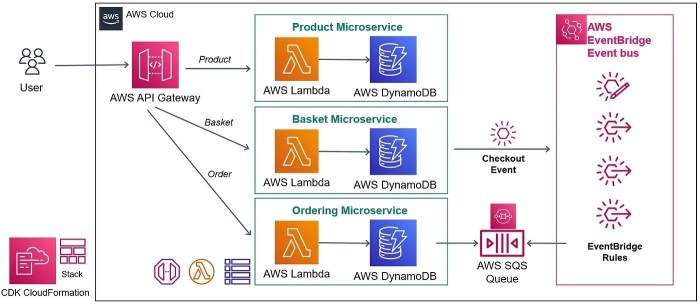
This guide provides a comprehensive overview of scheduling Lambda functions to run periodically, a critical component for automating tasks in modern c...

Navigating the Kubernetes landscape requires a clear understanding of its fundamental components: Pods and containers. This article provides a compreh...

In today's evolving business environment, developing a skilled and prepared team is essential for organizational success. This guide provides a compre...
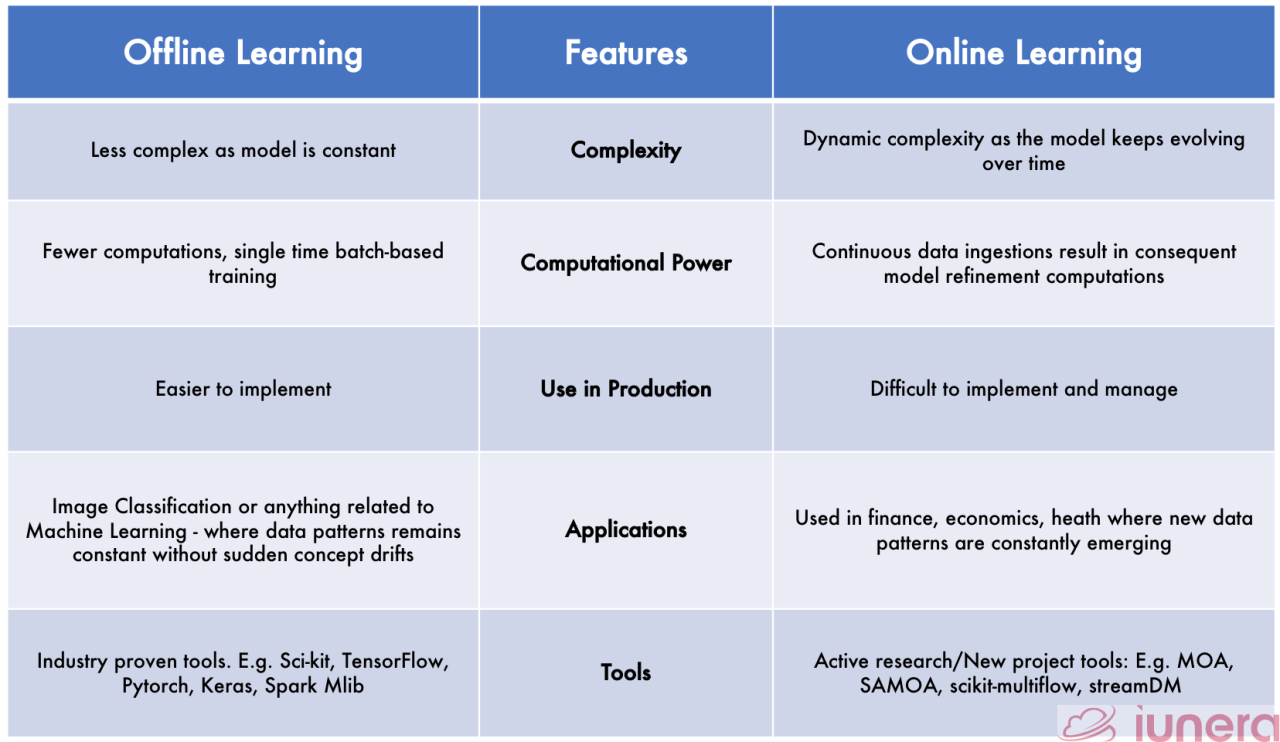
This article provides a comprehensive overview of online versus offline data migration, exploring the fundamental differences, advantages, and disadva...

Cloud Development Kits (CDKs) represent a significant advancement in cloud infrastructure management by enabling Infrastructure as Code (IaC) with fam...
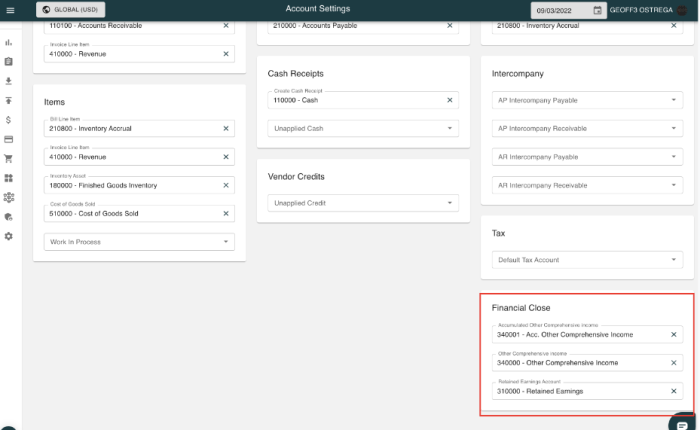
Configuration drift in security settings poses a significant threat to your organization's security posture, silently eroding defenses through unnotic...