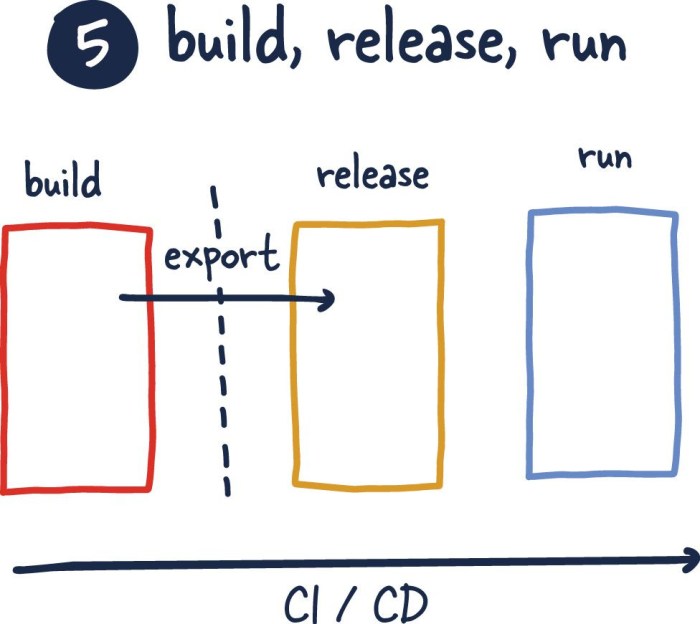
Separating Build, Release, and Run Stages: A Factor V Guide
This article provides a comprehensive guide to strictly separating the build, release, and run stages, outlining the critical importance of this pract...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a comprehensive guide to strictly separating the build, release, and run stages, outlining the critical importance of this pract...

This article explores the crucial role finance teams play in the emerging discipline of FinOps, a framework designed to optimize cloud spending and dr...

Ready to enhance your cybersecurity strategy with a proactive approach? This article explores the use of honeypots, a sophisticated technique designed...
This article delves into the critical challenges inherent in microservice architectures, such as network latency, security vulnerabilities, and comple...

This comprehensive guide explores the critical role of API Gateways in modern software architecture, delving into various design patterns, security co...
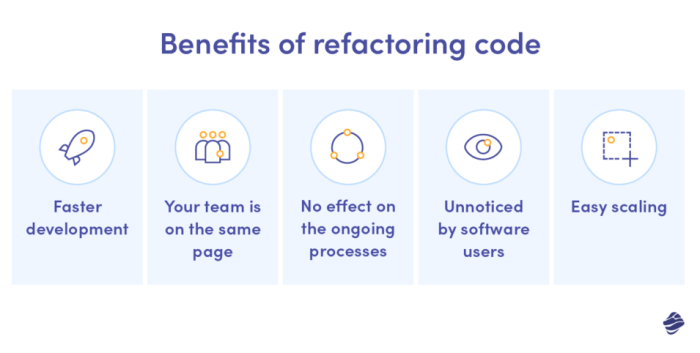
This comprehensive guide provides a deep dive into the critical process of code refactoring, offering practical strategies to improve your software's...
Effectively managing cloud budgets is critical for controlling costs and maximizing the value of your cloud investments. This comprehensive guide delv...

To fortify your cloud environment, a cloud vulnerability assessment is crucial. This guide provides a structured, step-by-step approach to identifying...
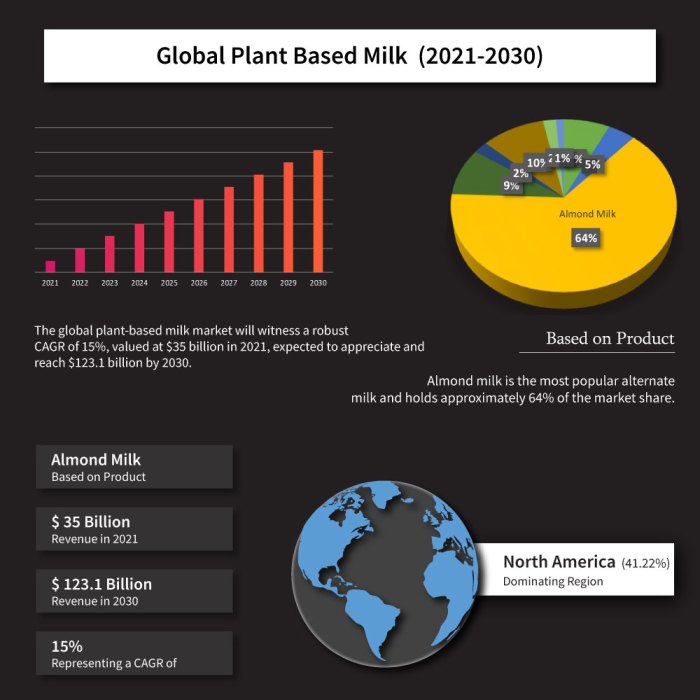
This article outlines a continuous approach to strengthening your security posture, emphasizing that it's an ongoing process rather than a one-time fi...
Cloud migration case studies provide valuable insight into the complex process of transitioning a business to the cloud. These detailed accounts offer...
Facing the evolving challenges of cloud security? This article provides a comprehensive guide to implementing a zero trust security model in your clou...

Distributed systems rely on leader election to designate a single node responsible for coordinating tasks and ensuring data consistency. This critical...