
Identify and Eliminate Waste: A Guide to Terminating Unused Cloud Resources
This comprehensive guide provides a detailed roadmap for identifying and terminating unused cloud resources, a critical step in optimizing cloud spend...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide provides a detailed roadmap for identifying and terminating unused cloud resources, a critical step in optimizing cloud spend...

In today's cybersecurity landscape, de-provisioning – the process of removing user access to systems and data – is a critical, yet frequently overlook...

Serverless computing simplifies application development by abstracting away server management, allowing developers to focus solely on code. This innov...

Ensure your critical systems remain operational even in the face of unexpected disruptions by mastering the principles of High Availability (HA) and D...
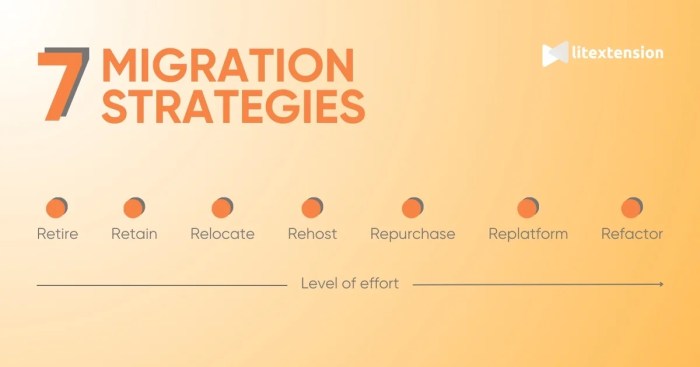
Application migration can significantly impact application latency, potentially leading to performance degradation if not carefully managed. This arti...
This article, "How to Design Applications with Cost in Mind," provides a comprehensive guide to building applications efficiently while adhering to bu...
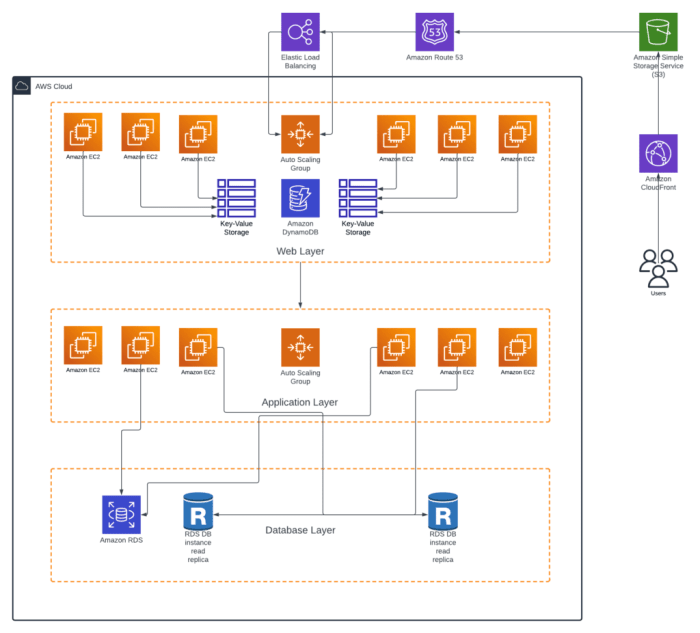
This comprehensive guide provides a step-by-step approach to refactoring applications into a serverless architecture, outlining the key considerations...
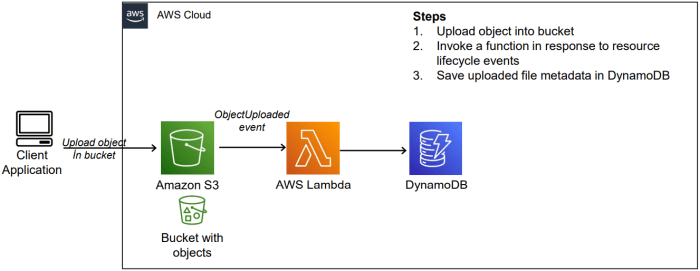
This article provides a comprehensive guide to triggering AWS Lambda functions in response to events within your Amazon S3 buckets, a key component of...
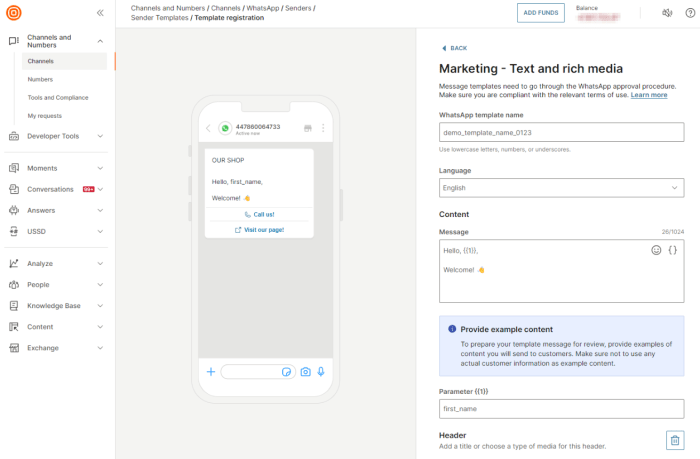
This comprehensive guide details the essential steps for designing and implementing a secure cloud landing zone, covering everything from defining sco...

This article provides a comprehensive overview of Cloud Security Posture Management (CSPM), detailing its core purpose in cloud environments and diffe...
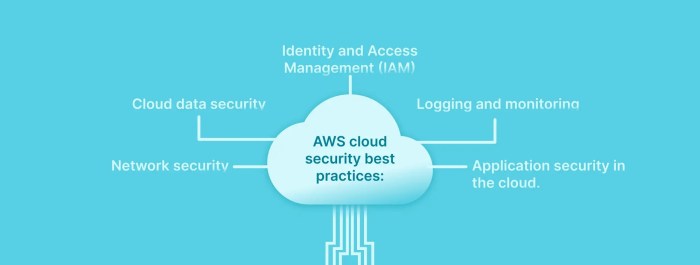
Migrating to the cloud demands a robust security strategy to mitigate emerging threats and vulnerabilities. This article outlines essential security b...

To effectively manage and optimize your cloud environment, understanding key performance indicators (KPIs) is paramount. This article provides a compr...